Data Security from the Inside Out

This is the third in a three-part series highlighting issues related to government insider threats
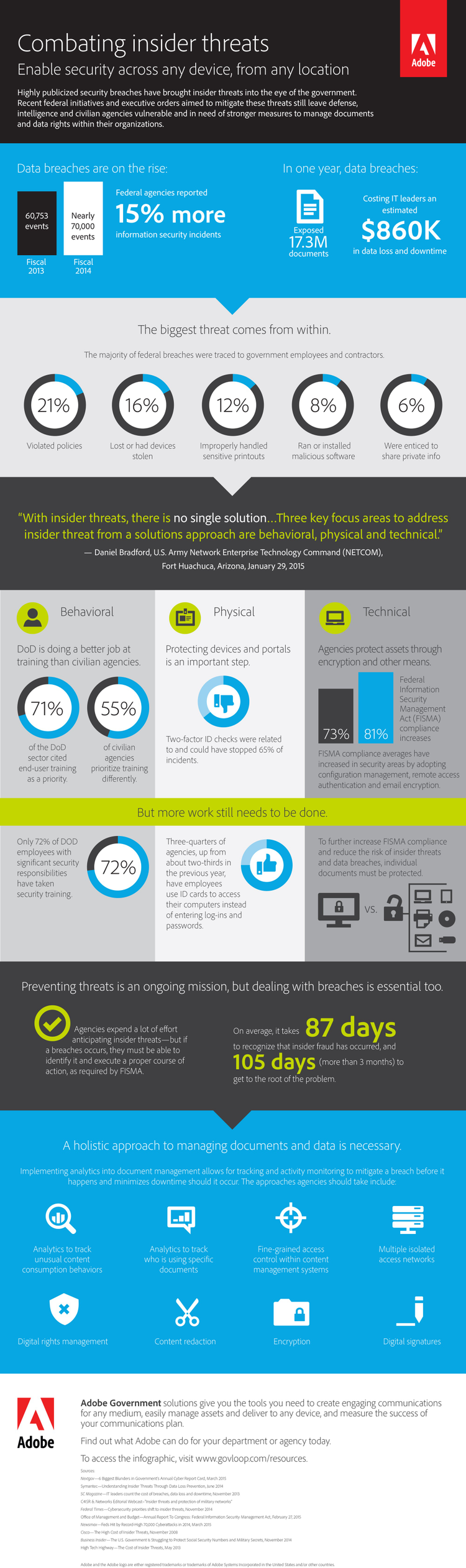
This week we have called attention to issues relating to cyber security in the workplace as part of National Cyber Security Awareness Month, which is essential given that agencies have reported 15 percent more information security incidents between fiscal year 2013 and 2014. The impact of insider threats, ranging from leaking sensitive information to journalists to physical threats to government facilities, can be devastating to our national security both here at home and abroad.
Data breaches have become the new norm, and hackers are going after the government as one of their prime targets. The ever-increasing cyber threat landscape has swiftly propelled cyber security to the top of our national security priority list. In one year, data breaches exposed 17.3 million documents costing agencies an estimated $860,000 in data loss and downtime. As agencies become more digital, sensitive documents including social security records, intellectual property and national security information are being stored electronically. Federal agencies must do everything possible to ensure that this information remains safe from both internal and external threats.
Detecting, preventing insider threats
As noted throughout this series, there are three key elements of information protection – physical, technical and behavioral – that are essential in preventing and detecting potential insider threats. We will examine the behavioral component now…
One way to prevent and detect breaches is to examine the profiles of individuals who access an organization’s protected information. By understanding a person’s behavior – such as what content they access, when and how often they access it and what they are doing with the content – a baseline knowledge of that individual can be created so that anomalies can be detected. Behavioral models and anomaly detection algorithms alert security staff of out-of-the-ordinary events and identify whether certain sensitive documents need to be analyzed for potential security breaches. Examples of unusual behavior include:
- Attempted access occurred from different locations (if a person is badged in a DC location, but opens a document in San Jose)
- Attempted access during odd hours of the day or night
- A higher than normal number of print jobs occurred (if a person prints five documents a day on average but then prints 500)
- A higher than normal number of downloads
- Multiple failed attempts at opening a document
With content management and rights management technology, security records associated with a sensitive document can help to identify meaningful deviations from normal behavior that signal malicious intent. Taking preventive measures even further, agencies can incorporate continuous monitoring and ongoing analysis of audit logs, which provide a complete picture of all users editing, accessing and being denied access to an organization’s content. This allows key personnel to gather and analyze complex datasets in real time to reveal when additional scrutiny is required and whether it is necessary to take decisive actions. Incident response teams can be notified automatically if protected content leaves sensitive networks open to unauthorized recipients.
By looking at the behavioral aspects, including content consumption patterns coupled with continuous monitoring, agencies can be proactive in discovering what may be unusual or suspicious activity—an important step in combating cyber attacks and one of the three areas to monitor in the fight against insider threats.
http://blogs.adobe.com/adobeingovernment/files/2015/10/adobe_DODinfographic_digrightsman8.jpg