Document Security Built for Life

This is the second in a three-part series highlighting issues related to government insider threats.
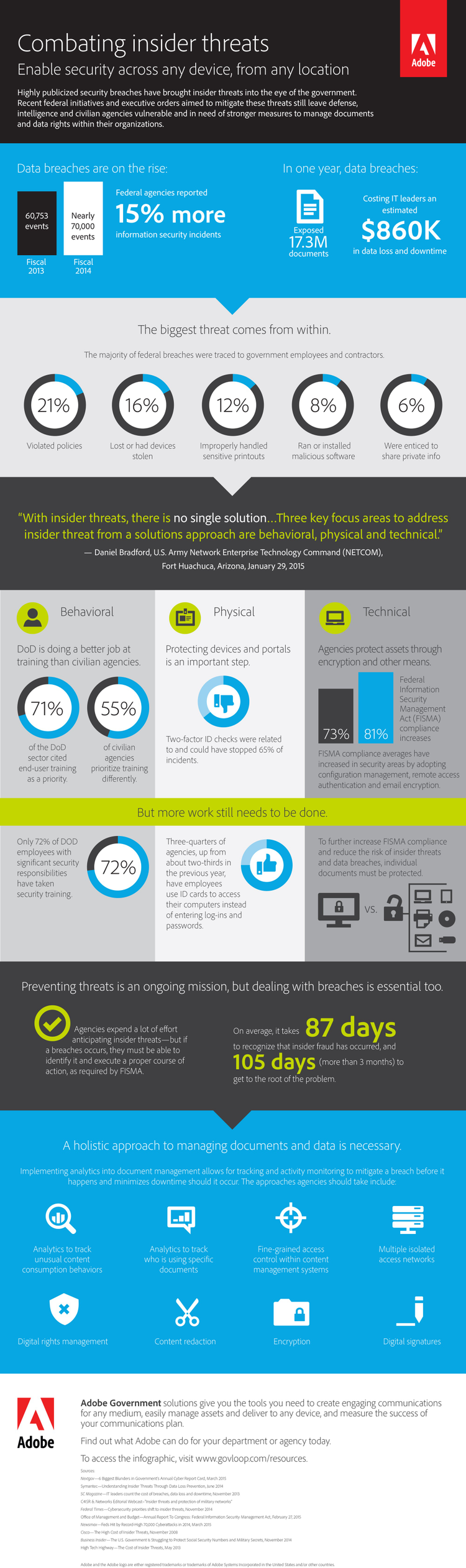
The threat to government documents is persistent, eminent and evolving, often taking significant time to even identify that an incident has occurred. On average, it takes 87 days to recognize that insider fraud has occurred, and 105 days (more than three months) to get to the root of the problem.
Securing information throughout its lifecycle
Content privacy, security and compliance are all important aspects of government business. Sensitive content is frequently exchanged between agencies, contractors, industry and other vendors within the supply chain. A government document is often protected within the safe boundaries of a firewall, but once this information is distributed outside of the firewall it is imperative that it remains secure throughout its lifecycle. The potential for insiders to misuse or accidentally leak information exists every time someone disseminates content.
Faced with insider threats, many government agencies are turning to encryption and other methods to ensure that their cyber infrastructure is safe, secure and resilient. Reports indicate that Federal Information Security Management Act (FISMA) compliance averages have increased from 73 to 81 percent in security areas by adopting configuration management, remote access authentication and email encryption.
However, not all encryption methods are the same. For instance, turning on whole-disk encryption really only defends against physical theft of the drives. When hackers find their way into the system, the data is decrypted automatically on read, which can then be exfiltrated and saved elsewhere. Turning on transparent encryption in the database may still be prone to attackers employing SQL injection or application exploits to gain access to the information, which again can be automatically decrypted, exfiltrated and saved elsewhere. In both cases, the information is forever lost and irretrievable.
A better technical approach is to leverage user-based encryption, specifically Digital Rights Management (DRM) which persistently protects sensitive information no matter where it goes. While an attacker can try to steal the end-user’s credentials to gain access to the encrypted information, the technology thwarts attempts to save the information in the clear. Furthermore, attempts at viewing the information can be detected and immediately revoked via remote shredding, which provides powerful capabilities to defenders performing incident response.
The bottom line: unless individual pieces of information are protected, any and all content is at risk. DRM-based encryption is user-centric and the content is encrypted independently, regardless of where or how it is stored. By encrypting the entire file, no matter where it goes, anyone wanting to access it must authenticate themselves. With built in access controls enforced at the file layer, agencies can monitor and track information as it is shared outside of the organization. Unlike traditional enveloped encryption, DRM has several strong security measures, including:
- Users have the ability to set or reset content permissions before and even after content has left the network
- Documents can be restricted from editing, printing or copying. They can also be revoked, so access expires and terminates after publishing
- For users needing to view sensitive documents in an offline environment, files can be granted offline leases
- Content protection remains intact regardless of the number of copies or whether a document is renamed
With DRM technology, government organizations can identify, track and control changes to maintain data security throughout the lifecycle. From a technical perspective, access controls built into the files themselves reduces the risk of inappropriate information sharing by determining where documents are going, and detecting where information might be leaking. Agencies can effectively utilize DRM technology as a part of a comprehensive strategy to protect both the integrity of their workforce as well as the information that needs to be safeguarded at all times—a much needed approach toward eliminating the risk of insider threats. Stay tuned for part three in our series – Data Security from the Inside Out.
http://blogs.adobe.com/adobeingovernment/files/2015/10/adobe_DODinfographic_digrightsman8.jpg