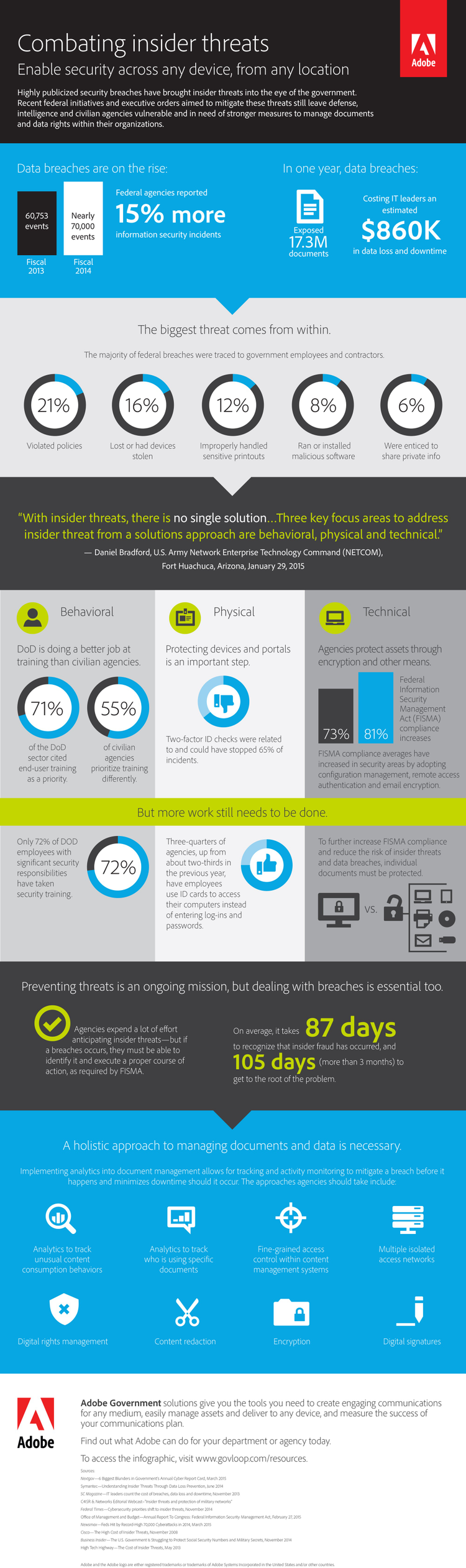
October marks the observance of National Cyber Security Awareness Month (NCSAM). Now in its 11th year, attention among federal agencies to this month-long initiative has never been more pressing. During the week of October 5–9th, NCSAM will focus on “Creating a Culture of Cybersecurity at Work,” which will certainly include a look at the insider threat given that a majority of breaches were traced to government employees and contractors – 21 percent violated policies and 16 percent lost or had devices stolen.
The insider threat has become an essential component of every agency’s comprehensive security program, and these threats are one of the most potentially dangerous forms of network compromise. Agencies need to reinforce their current strategies against data breaches and cyber threats – whether these attempts are malicious or accidental in nature – by focusing on stronger measures to manage documents and data rights.
Information right of way
So how can agencies protect data and information independent of the device or location in which that information is stored? By leveraging physical, technical and behavioral controls, organizations can more effectively safeguard sensitive information from external and internal threats.
When we think of physical security, we often think of locks on doors, fences or guards. With a guard, access control to sensitive areas can be made based on observations about the individual, their destination and the environment. Not only can they perform strong identity checks, but they can also make decisions based on other attributes, like time-of-day, individual appearance or answers to questions. Organizations can use similar techniques to control the access to sensitive information by employing an attribute-based control access (ABAC) model. Unlike traditional access control methods, ABAC enables dynamic, fine-grain access control decisions based on attributes about the user, the informational asset and the environment.
Government agencies are able to minimize insider threats by using content controls that, in essence, specify which users or groups of users have access to digital objects in their repository. With an ABAC system, paragraphs, images, videos, titles and even bullet points can be assigned with multiple security attributes, similar to classification levels, International Traffic in Arms Regulations (ITAR) requirements and environmental variables.
For example, imagine a report, which is authored as a web page, and is comprised of text, images and video, all containing different security markings. When an individual authenticates into the system to view the report, they can only see the portions that they are authorized to see, based on their own security attributes. Another individual with a separate set of attributes, such as a higher clearance level, different citizenship status or physical location, would see a different dynamically redacted report. Furthermore, should any object change within the repository, like a reclassification of a video, all pages referencing that object would automatically be updated accordingly.
In addition, protecting devices and portals through encryption and two-factor ID checks, such as using Common Access Cards (CAC) in conjunction with passwords can dramatically increase the protection of documents and information. In fact, it is reported that two-factor ID checks could have stopped 65 percent of incidents. Visit our blog throughout the week as we detail the other two components to help position your agency for a more structured, comprehensive and effective insider threat program.