Securing the Supply Chain and High Value Assets in a Zero Trust Environment

Image source: Adobe Stock.
National Cyber Security Awareness Month (NCSAM) is a time to remember that we must continually work to improve security posture.
In many organizations, including government, security has largely been accomplished with perimeter-style defenses, like multiple network zones, firewalls and encryption. But upon closer inspection, we can find a more intelligent way to help protect the infrastructure.
Some security compliance frameworks state that data encryption should happen at rest and in motion. Yet all encryption methods aren’t equal. Technology decision-makers must evaluate each approach against the threat models for the environments they manage.
For instance, whole-disk encryption defends against physical theft of the drive. Moving up the stack to network protection measures like Secure Sockets Layer (SSL), Transport Layer Security (TLS), or virtual private networking (VPN) also can pose potential issues. Data is encrypted at one end, only to be decrypted at the other end and could be exposed to unauthorized activities. Application security measures like transparent encryption in the database are potentially prone to Structured Query Language (SQL) injection attacks and application exploits to access information.
To help combat potential security threats, IT security practitioners have started adopting a Zero Trust posture with content-level data protection technologies, like Digital Rights Management (DRM) as shown in the figure below.
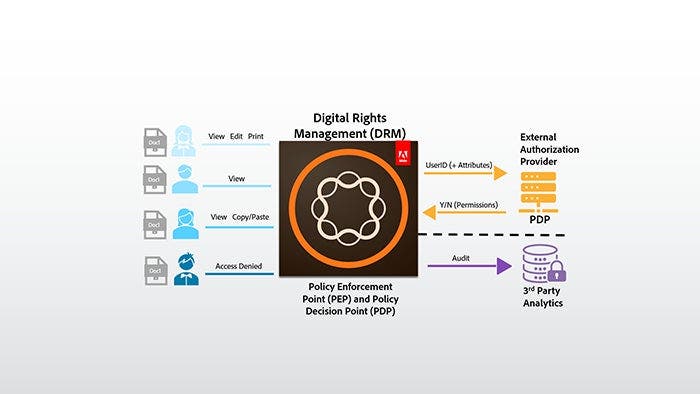
What is “Zero Trust?”
“Zero Trust” is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access.
According to “Zero Trust Networks: Building Secure Systems in Untrusted Networks” by Evan Gilman and Doug Barth, a Zero Trust network is built upon five fundamental assertions:
- The network is always assumed to be hostile.
- External and internal threats exist on the network at all times.
- Network locality is not sufficient for deciding trust in a network.
- Every device, user, and network flow is authenticated and authorized.
- Policies must be dynamic and calculated from as many sources of data as possible.
There are two great use cases for moving toward a Zero Trust environment with content-level data protection.
The first case is from how the Department of Defense (DoD) strengthened its supply chain by protecting defense information. Recently, the DoD developed the Cybersecurity Maturity Model Certification (CMMC). CMMC builds upon Defense Federal Acquisition Regulations Supplement (DFARS) Clause 252.204-7012, Safeguarding Covered Defense Information and Cyber Incident Reporting, by adding a verification component with respect to cybersecurity requirements and mapping these controls and processes across several maturity levels that range from basic to advanced cyber hygiene.
The second case is the Department of Homeland Security’s (DHS) Continuous Diagnostics and Mitigation (CDM) program for tools needed to protect sensitive information and high-value assets (HVA). HVAs fall into three categories:
- Informational value: The information or information system that processes, stores, or transmits the information is of high value to the government or its adversaries.
- Mission essential: The agency that owns the information or information system cannot accomplish its Primary Mission Essential Functions (PMEF), as approved in accordance with Presidential Policy Directive 40 (PPD-40) National Continuity Policy, within expected timelines without the information or information system.
- Federal Civilian Enterprise Essential (FCEE): The information or information system serves a critical function in maintaining the security and resilience of the federal civilian enterprise.
Agencies also must monitor protection compliance related to HVAs containing personally identifiable information (PII). Both of these two use cases are underpinned by complying with the National Institute of Standards and Technology’s Special Publication 800-171 (NIST SP 800-171).
“Zero Trust” means users must prove they can be trusted
The backbone to a successful Zero Trust environment is a process that leverages micro-segmentation and granular permissions based on users (or applications), devices, and a trust decision. It’s about using these and other technologies to enforce the idea that no one and nothing has access until they’ve proven they should be trusted.
One key component to Zero Trust is the Control Plane, which decides whether an authenticated user and device are authorized to access a protected resource. The Control Plane provides fine-grained policy decisions that can be based upon roles, location, time of day, or type of device, to name a few.
But the Control Plane is only part of the solution.
Digital Rights Management (DRM) provides security down to the data level
To extend Zero Trust to content-level data protection, which is critical for federal, state, and local government agencies, one can use Digital Rights Management (DRM). DRM is a data-centric technology that helps protect documents and content containing sensitive information like Personally Identifiable Information (PII), Protected Health Information (PHI), Controlled Unclassified Information (CUI), and Intellectual Property (IP). In order for a DRM system to enforce Zero Trust principles down to the data level, the following requirements are mandatory:
- Persistent protection: This can be thought of as firewalls for your documents. But since documents are widely distributed, this needs to be provided by encryption at the file format level. This means that the file stays more secure, regardless of whether it’s at rest or in transport in cloud environments like Microsoft Azure and Amazon Web Services or on premise.
- Integration with the Control Plane for dynamic authorization decisions: The DRM system must be able to enforce the Control Plane’s dynamic authorizations to documents, like an Adobe PDF, or Microsoft Word, Excel, and PowerPoint, already distributed, regardless of their location. For example, documents moved to a USB drive must still enforce dynamic authorizations. The DRM server can also be the Policy Decision Point if necessary.
- Real-time streaming of document interactions to the Control Plane: Streaming document interactions back to the Control Plane in real time provides much-needed intelligence for risk/trust decisions. For instance, what time and from where did Alice print that document? Did Bob read the last page? Or copy content from the document? With these requirements met, Zero Trust is available at the data level. This provides powerful new mitigations against potential attacks. For example, giving access to a document by a user from their normal location during typical working hours would be granted, but access from a new location at different working hours might initiate an out-of-band authentication (phone call, mobile phone push request, etc.) before granting access.
Improve data security with Adobe
As the security landscape grows increasingly complex and challenging, traditional perimeter-style security architecture need to be rethought. This has given rise to new architectures, like Zero Trust, that take a different approach.
Adobe continues to be recognized as an industry leader in DRM, especially in the public sector. By assuming that nothing is trusted inside or outside the perimeter, Zero Trust aims to dynamically verify all access to system resources. With DRM, we can extend Zero Trust principles down to the content level and provide much stronger protections and mitigations against potential issues.
Special thanks to Steven Gottwals for his contributions to this article.